51% Attack

51% attack refers to an attack on a blockchain – usually bitcoin's, for which such an attack is still hypothetical – by a group of miners controlling more than 50% of the network's mining hashrate, or computing power. The attackers would be able to prevent new transactions from gaining confirmations, allowing them to halt payments between some or all users. They would also be able to reverse transactions that were completed while they were in control of the network, meaning they could double-spend coins.
They would almost certainly not be able to create a create new coins or alter old blocks, so a 51% attack would probably not destroy bitcoin or another blockchain-based currency outright, even if it proved highly damaging.
While 51 percent attackers can’t create false transactions for someone else unless the attacker somehow gets access to that person’s unique digital signature, they can reverse their own transactions and prevent the confirmation of new transactions. In a sense, you can’t really steal someone else’s cryptocurrency through a 51 percent attack. However, you can falsely send your own cryptocurrency to someone else, but then reverse that transaction and end up keeping the crypto.
You can reverse a transaction by essentially rendering it obsolete. This entails creating a new chain that doesn’t include the previously recorded transaction you’d like to “reverse.” In doing this, you can end up “spending” the same coins twice.
This is why people also refer to a 51 percent attack as a “double spend attack.” Coinbase’s blog post on the recent Ethereum Classic attack has a clear explanation of how this works. Paraphrasing it here, a miner or miners (let’s call her person A) with 51 percent control of a network could send person B coins while secretively starting a new, alternative block record. In that new record, person A would include a transaction with the same coins she “sent” to person B. Person A can then build off that new record, adding more blocks until it becomes the longest chain. This makes it the new canonical chain and renders the original transaction between person A and person B invalid, since those same coins now exist in a canonically valid block. Here’s a handy graphic borrowed from Coinbase security engineer Mark Nesbitt:
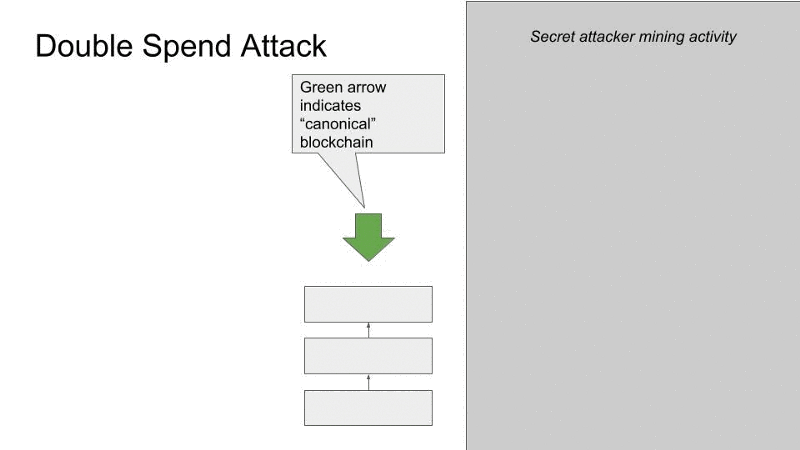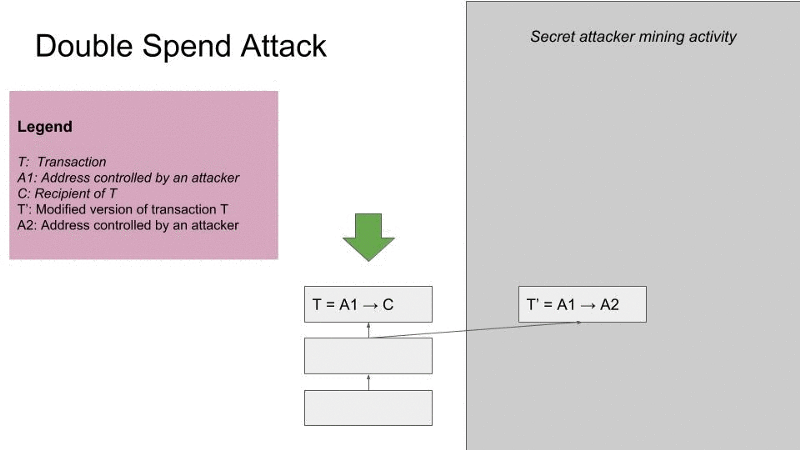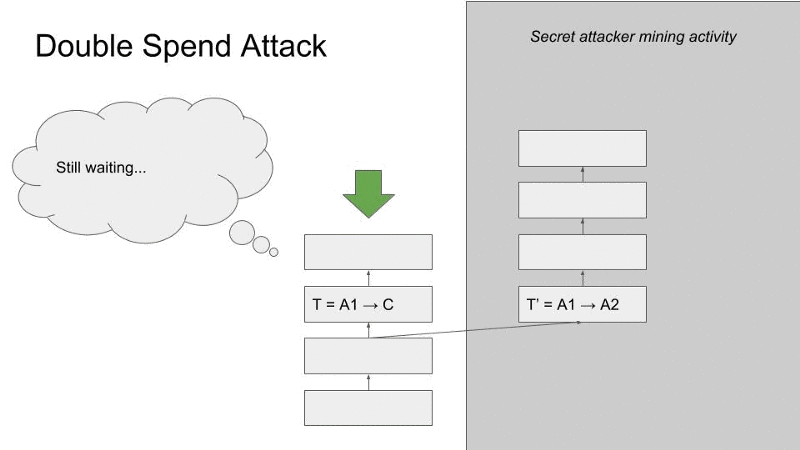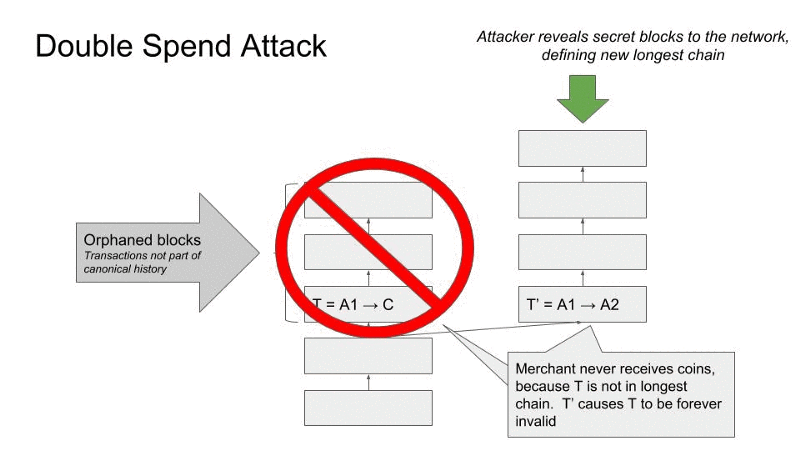
In the case of a dishonest buyer sending cryptocurrency to a vendor, that vendor could easily end up sending wares to the buyer while the buyer stealthily creates that new, longest chain. The dishonest buyer gets what they paid for while invalidating the transaction that would have sent the vendor the coins it cost to buy their product.
What would it take to carry out a successful 51 percent attack on bitcoin? Ethereum? What about Zcash?
There’s a handy website that answers all of these questions called Crypto51. It lays out the how much it would theoretically cost to effectively attack networks ranging from bitcoin and Ethereum to the lesser known likes of Vertcoin (which succumbed to a 51 percent attack in December) and Catcoin. Attacking the bitcoin’s network this way would cost about $340,232 per hour, according to the website. Ethereum would cost $103,487 per hour, and Zcash would cost $12,989 per hour. A 51 percent attack on Catcoin, says Crypto51, would cost a whopping $0 an hour. What are we waiting for?
The vulnerability is fundamental, stemming from the architecture of bitcoin-like cryptocurrencies. This means that by making some changes to the process of generating blocks and confirming transactions, it can be eliminated. One example of how this can be done, demonstrates the recently introduced the currency of PPCoin. It implements the Proof-of-Stake principle instead of the standard Proof-of-Work principle. Its meaning is that the probability of generating a block is not affected by the generation power, but by the number of coins that the miner already has. That is, to generate 51% or more of the units must have 51% of coins, which makes the attacker the most injured member of the network. Thus, commercial hacking is excluded completely, and destructive becomes difficult and expensive, Nevertheless, the technology is very controversial and carries other dangers, such as the possibility of monopolization of the transaction process by one major holder of funds. In other words, it turns out the same Issuer-the Central Bank, voluntarily distributing the currency in the economy. Strictly speaking, ppcoin uses hybrid technology — and Proof-of-Work and Proof-of-Stake at the same time. Such a system needs to be time-tested, since removing one problem can give rise to a dozen others.
This vulnerability is part of the lives of all involved in various cryptocurrencies. Also, this is a very likely cause of death of the young currency "standard design", which does not have additional protection mechanisms. Moreover, this problem is fundamental and will not disappear. Night is a nightmare or a Ghost threat — everyone decides for himself.