Cracking wallet.dat using Hashcat
Password cracking is an art, consistent success of which requires a fine-tuning approach.
Don’t forget that luck and good hashrate will also help you recover lost passwords and access to the coins.

Password cracking is an art, consistent success of which requires a fine-tuning approach.
Don’t forget that luck and good hashrate will also help you recover lost passwords and access to the coins.

Copy wallet.dat file and bitcoin2john.py to a directory. If you work under Windows, copy both files to the Python folder or add Python links to environments.
Using the command line or terminal, execute:
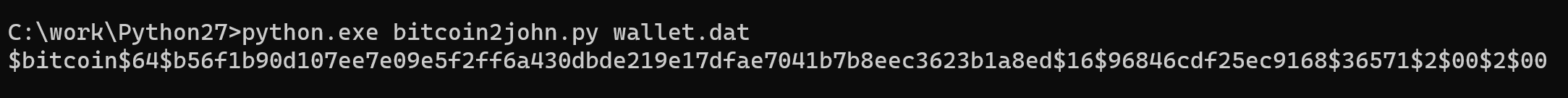
python bitcoin2john.py wallet.dat
Take the line that starts with $bitcoin and place it in a file called hash.txt in the working directory.
Note: If you’re reading this because you’ve forgotten your password and can't crack it yourself, you can share this hash with a wallet recovery service. Cracking this hash will not allow them to access your Bitcoins unless they also have access to your wallet.dat file.
Save the desired dictionary to a file called wordlist.txt which is in the working folder with your hash.txt file. First, we are going to run a straight-up dictionary attack. This means that password has to be found in your wordlist exactly - with a correct case, special characters, etc.
Try it this way first, with some hardware optimization parameters:
/opt/hashcat/hashcat64.bin -a 0 -m 11300 ./hash.txt ./wordlist.txt -O -w 3
If that doesn't work, try this:
/opt/hashcat/hashcat64.bin -a 0 -m 11300 ./hash.txt ./wordlist.txt
On Windows:
cd /folder_with_these_files/hashcat64.exe -a 0 -m 11300 hash.txt wordlist.txtIf your session completes successfully, you will see an output with your password. If the session is completed and you aren’t sure it was successful, running the command as follows will show you all successfully cracked passwords for a given target:
/opt/hashcat/hashcat64.bin -a 0 -m 11300 ~/hash.txt --show
If the output of the above command is blank, the password has not been cracked yet.
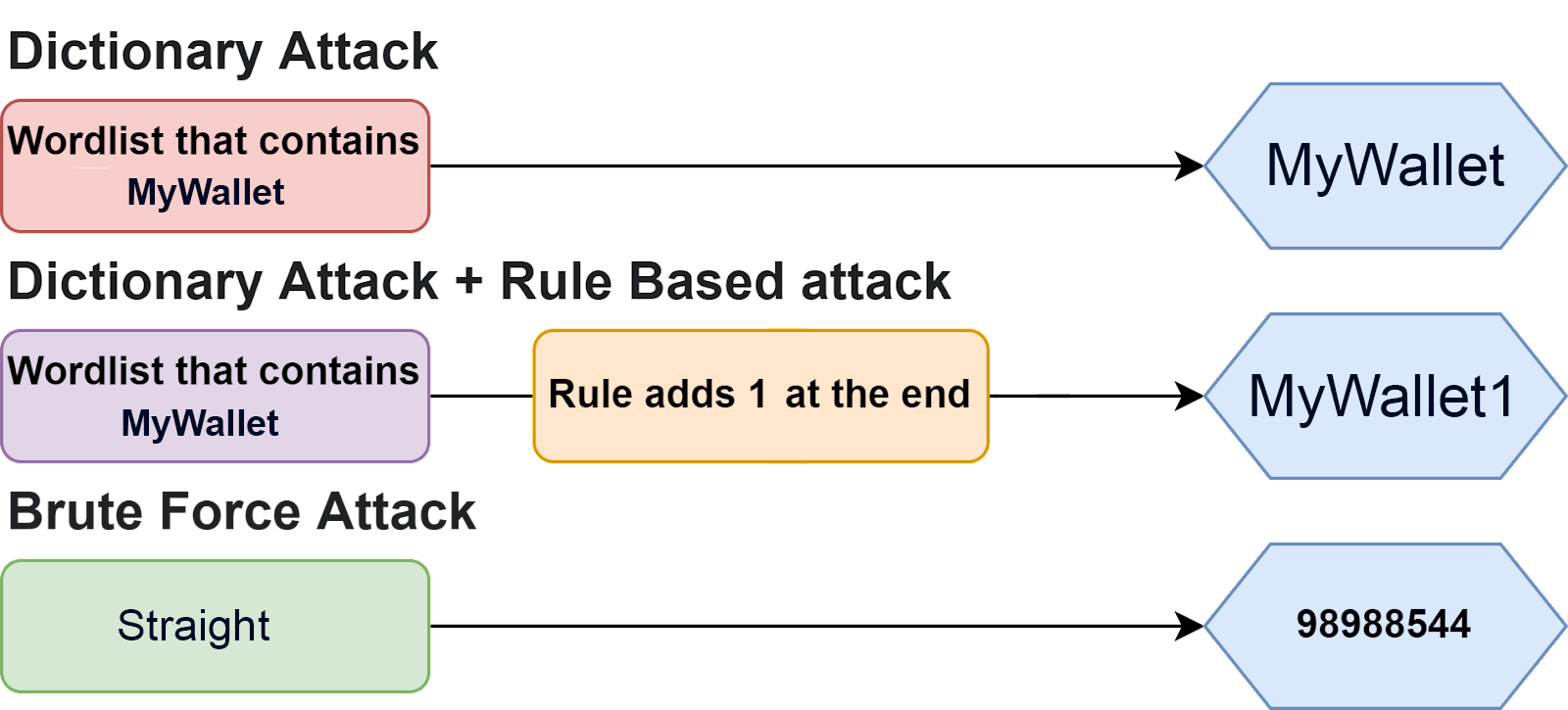
As humans, we are pretty dumb when it comes to making passwords. We can add !, 1, or all capital chars to make them more secure. Cracking password MyWallet1 with the help of a dictionary with MyWallet you will not get lucky but using a rule-base can help.
Download Hob0Rules and place it in /opt/rules/.
Then execute:
/opt/hashcat/hashcat64.bin -a 0 -m 11300 ./hash.txt ./wordlist.txt -r
/opt/rules/Hob0Rules/hob064.rule -O -w 3
Windows:
hashcat.exe --stdout wordlist.txt -r hob064.rule -m 11300 hash.txt
For example, the password is Julia1984.
In the traditional Brute-Force attack, we require a charset that contains all upper-case letters, all lower-case letters, and all digits (aka “a mix of alpha-numeric”). The total number of passwords to try is Number of Chars in Charset ^ Length. The Password length is 9, so we have to iterate through 62^9 (13,537,086,546,263,552) combinations. Let's say we crack with a rate of 100 M/s (slow Intel i3 processor), this requires more than 4 years to complete.
But let’s use a mask attack. We know that the name starts with a capital letter and four digits at the end.
Execute:
hashcat64.exe -m 11300 hash.txt -a ?u?l?l?l?l?d?d?d?d
In a nutshell, with the mask attack we can reduce the keyspace to 52*26*26*26*26*10*10*10*10 (237,627,520,000) combinations. With the same cracking rate of 100 M/s, this requires just 40 minutes to complete.